
In the hacking world, there are all sorts of tricks employed to get users to trust emails enough to open an attachment or click a link. Once, users become savvy to one particular tactic, attackers move on and change things up.
For example, most users now know to be very suspicious of file attachments in emails from unknown senders. A lot of network security strategies will include an element that scans attachments before they are fully opened for any signs of malware.
That wasn’t always the case. About 15 years ago, file attachments were the most popular method for spreading viruses and other types of malware. But users became aware, and as a result, they became less successful for the attackers.
So, the attackers switched tactics. Users were now suspicious of file attachments in emails, but links were still trusted. A person clicks links all day long in the course of their work, so this became a better way for hackers to perpetrate attacks.
Now, over 85% of phishing emails contain links to malicious sites or documents rather than file attachments.
Another way that hackers have changed tactics to make phishing emails more successful is to link to a document type that many users trust, PDF. The Adobe PDF format is one of the most recognized in the world. Last year alone, 300 billion PDFs were opened in Adobe apps.
Many people don’t think that a PDF can contain ransomware, viruses, or other forms of malware, but it can. This is why links to PDF documents are particularly dangerous.
What Does a PDF Attack Look Like?
If you visit our Hacker’s Toolkit page, you can get a rare glimpse into three common forms of hacks from the attacker’s perspective. The first on the page shows a common ransomware attack that happens through a link to a PDF inserted into a convincing phishing email.
The attack begins in the email inbox as many of them do. The user receives an email from the IRS that appears at first glance to look legitimate and not particularly strange or threatening.
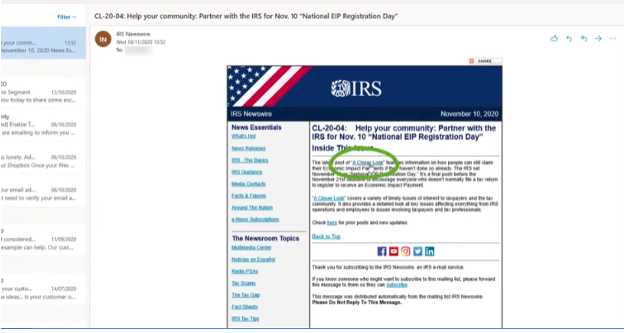
The email is inviting the user to “help your community” and looks like it could contain some helpful information. Not suspecting a fake, the person clicks the link to learn more, which opens an official-looking PDF document that appears legitimate.
Even the website hosting the PDF has that lock icon showing that it’s secure, which gives the user another reason to feel nothing is out of the ordinary.
74% of all phishing websites use HTTPS to give users a false sense of security.
After reviewing the information (yes, hackers go so far as to create realistic documents to fool users), the person closes the PDF and returns to their work, not suspecting anything.
Then, when the person’s browser window is closed, a ransomware message appears on the screen. That innocent-looking PDF infected their device with ransomware as soon as they opened it. Now all their files are locked and inaccessible and the ransomware is making its way through the network.
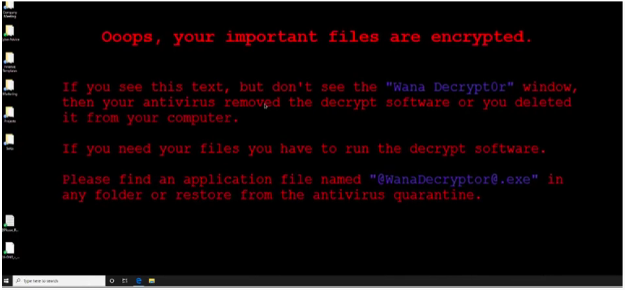
How Did That Happen?
From the hacker’s side of things, they’ve spent time setting up this trap to fool as many people as possible. Once the PDF and website are in place, the hacker drafts the email message and then sends it out to millions of users. They only need a small percentage to take the bait and pay them the ransom for it to be worth their time and effort.
PDF files may look fairly innocuous on the surface, but they can contain elements that harbor ransomware, viruses, spyware, trojans and other types of malware.
Here are some of the ways that a hacker can turn a PDF document into a phishing trap:
- Embed malware in multimedia like video and audio
- Use JavaScript hidden in the PDF reader to initiate a malware infection
- Instruct a computer to initiate a command through hidden code
How to Prevent PDF Ransomware & Malware Infections
There are a few safeguards you can put in place to help prevent falling victim to an attack through a PDF. These include:
- Train Users: Ensure users understand that links are just as dangerous as file attachments and that document types they may tend to trust, like PDF, can carry malware.
- Disable Adobe JavaScript in Your PDF Reader: Open the settings of your PDF reader (Adobe Reader or other) and look for a setting that allows you to disable JavaScript for Acrobat documents.
- Don’t Enable Macros in Email Attachments: Disabling macros for email attachments can help you avoid a malware infection from a PDF as well as a Microsoft document.
- Keep Your PDF Reader & System Updated: Avoid falling victim to an exploit you could’ve avoided through an update. Keep your PDF reader, other software, and your operating system regularly updated.
Are Your Systems & Users Properly Prepared for the Next Phishing Email?
Onsite Techs of Rhode Island can help your business take a look at your current security protections and user awareness and help you better protect yourself from a cyberattack.
Contact us today to schedule a consultation at 401-773-7766 or book a video call now.


