
We often hear about virus infections, ransomware attacks, and data breaches from the victim’s perspective, but rarely do we see it through the eyes of a hacker.
By trade, hackers operate in a stealth environment and do everything they can to not be tracked while they’re attacking businesses of all kinds to steal data, extort the company using ransomware, or take over systems for their own use.
One of the most damaging events that can happen to a company is to become the victim of a cyberattack. Many small businesses think they are “too small” for a cybercriminal to bother with, but the opposite is true. Because smaller companies tend not to have the same cybersecurity protections as larger organizations, hackers see them as low-hanging fruit.
Approximately 43% of cyberattacks target small businesses, and those unlucky enough to become victims are faced with an average cost of $200,000 per incident.
So, not fully understanding just how easy it is for hackers to breach their systems and not being protected can put a small company out of business.
In our efforts to fully educate the Rhode Island community about the dangers out there waiting to attack their networks, we’ve put together the Hacker’s Toolkit.
This page provides a rare glimpse into the world behind the computer screen. We provide videos showing three different types of common hacks and what they look like from both a user’s and hacker’s perspectives.
You may just be surprised to see how easy it is for a user to get fooled and your company’s network and devices to be breached.
We’ll go through an overview of each of the three hacks below.
Ransomware Delivered via an “IRS” PDF
The first of the three hacks involves a common occurrence that happens in offices every day… a user getting fooled by a phishing email.
The user receives an email from what appears to be the IRS about some type of community program. There is a link to a PDF, so the user feels fairly safe clicking it because it’s not a file attachment (which they’ve been taught can be dangerous to open) and it’s a PDF. They haven’t ever run across any information about a PDF causing a malware infection.
From the hacker’s point of view, they know immediately when the user clicks that PDF link and opens their cleverly faked document. The hidden code does its job and infects the user’s system with ransomware.
They now have the opportunity for a big payday of several thousands of dollars because the ransomware has encrypted all the documents on that user’s PC and is quickly traveling through the network to encrypt data on other devices and any syncing cloud storage.
As of the first quarter of 2021, the average ransomware demand was over $220,000, up 43% from the prior quarter.
A Fake Login Page Is Used to Steal User credentials
In the next attack, a hacker conducts a man-in-the-middle attack to steal a user’s credentials and then log into the system as that user.
The attack begins with a spoofed administrative email from Office 365 asking the user to review two messages that have been held up in the spam filtering system.
If the user doesn’t notice a slight difference in the sender’s address that is a few characters off from Microsoft’s actual email domain, they can easily be fooled by the fake.
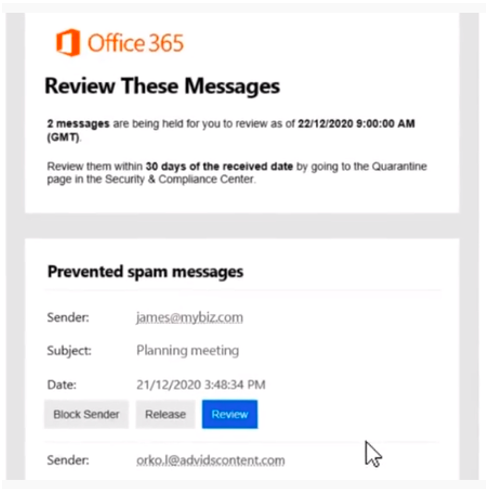
As soon as the user clicks the link to review, they’re taken to a Microsoft login page appearing to be legitimate, so they enter their password to gain access.
But on the other end of the internet, the hacker was just able to grab that person’s user name and password and now can access their Microsoft account.
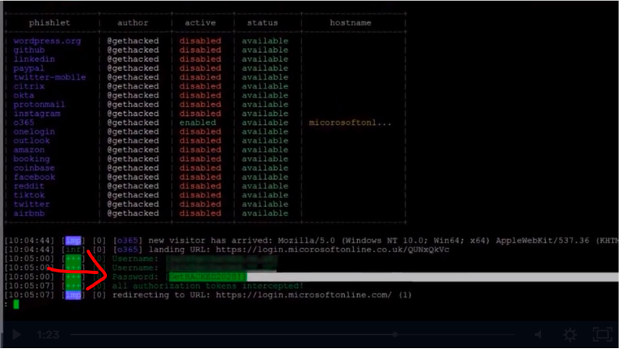
The hacker can now steal data, send out an email on the user’s email address, change security settings, plant ransomware, and much more.
How One Missed Update Can Lead to a Data Breach
Putting off the operating system and software updates is a common habit of users. They don’t want to interrupt what they’re doing, especially if an update means they have to reboot.
But what those users don’t know is that hackers are always looking for vulnerabilities in any new system, software, or feature addition to existing software or an OS.
Hackers monitor systems for outdated versions of software and then launch an attack that exploits the unpatched vulnerability. Once they’ve hacked the system, they’re often able to run malware code, take over a device for crypto mining, steal sensitive customer or employee information, or perform hundreds of other types of attacks.
Are You Really Sure Your Company’s IT Security Has You Covered?
Onsite Techs of Rhode Island can work with your business to assess your current IT security systems and user training to see what else you may need to be fully protected.
Contact us today to schedule a consultation at 401-773-7766 or book a video call now.


